Hardening WordPress Security: Tutorial for beginners

Having hard-luck stopping brute-force attacks on your site? Done with all security implementation but still under heavy DDoS? Website developers need to understand security issues and take steps towards hardening WordPress security.
With the growing impact of the Internet on all facets of life, websites are increasingly dealing with private and sensitive customer data. Indeed a security breach can lead to hacking your website. And can result in a major security lapse for well-established businesses. Also, it can potentially lead to irreparable damage to your reputation. As a web developer, you need to be able to assess the risks you’re facing.
Hardening WordPress security is a complicated topic. Here at Templatetoaster WordPress theme generator, I will help you gain an overall better understanding of WordPress security. In this tutorial for beginners, I also explain techniques to minimise and manage the security risks to your WordPress website. Most of these techniques are general and are beneficial for other Content Management Systems like Joomla, Magento etc.
Table of Contents
- What is WordPress Security Hardening?
- WordPress Security Issues
- What makes WordPress a Target for Hackers?
- WordPress Vulnerabilities
- Hardening WordPress Security
- Methods for Hardening WordPress Security
- Checking if WordPress Site is hacked
- Fixing Hacked WordPress Site
- WordPress Security Best Practices: Risk Reduction over Risk Elimination
- Security – Being aware and involved
- How TemplateToaster helps in Hardening WordPress security?
What is Hardening WordPress Security?
WordPress is a popular content management system and a target for hackers. According to W3Techs, the WordPress platform accounts for more than 25% of the websites worldwide. It is quite obvious that WordPress is not just a blogging platform. A majority of WordPress sites serve a broad range of other purposes. However, the worst nightmare for a WordPress developer is to see a malicious hacking attack on his site.
Hacks are very much common and happening frequently, with 38.9% of developers reporting a compromise in the last 12 months. In general, WordPress Security Hardening means taking precautionary and preventive steps to lock down your WordPress website. This would essentially prevent hackers and vulnerabilities from affecting the website or blog.
Certainly, hacks are very much common and happening frequently, with 38.9% of developers reporting a compromise in the last 12 months.
Why is WordPress Security Hardening Need of the Hour?
Security is the most important concern for organisations these days. A well-known and reliable resource of information related to web application security is the OWASP, a non-profit online community. The Open Web Application Security Project creates articles, tools, and technologies on web security. Their website is a comprehensive resource for information on the latest vulnerabilities, threats, attacks and countermeasures.
Here at Templatertoaster website maker and WordPress theme builder, Let us look at security from a WordPress standpoint and the details of WordPress vulnerabilities and security issues. We will also try to understand the strategies and techniques for hardening WordPress security.
Hardening WordPress Security Issues
Some people believe WordPress is prone to security vulnerabilities and inherently not being a safe platform for secure businesses. Many times this can be true because of series of reasons. To enumerate, as per a Q2 2016 report by Sucuri, WordPress at 74% continues to lead the number of infected websites they worked on.
In most cases, website hacking occurs primarily since users continue to follow industry-proven security worst practices. These include using obsolete WordPress software, improper system administration, unmanaged credentials’ handling and more. Most beginner WordPress users lack the necessary knowledge, on hardening WordPress Security, which makes their websites vulnerable. Advanced users also have the opinion that security practices once implemented will protect their websites forever. They are not aware of the need to revise, review and update the security measures regularly.
What makes WordPress a Target for Hackers?
As per a recent investigation, reported by WordPress security outfit WP White Security, 73% of the 40,000 most popular WordPress are vulnerable to attack.
To point out, WordPress is the most popular CMS and this has resulted in an ecosystem that includes over 42,000 plugins. This is to say, plugins are a very important asset to a WordPress site. An average of over 10 plugins is in use on every website. The foremost advantage of WordPress is its extensibility. However, it is also the cause of the vast number of WordPress security vulnerabilities. As per a survey conducted by Wordfence, around 61.1% of WordPress sites are customised substantially.
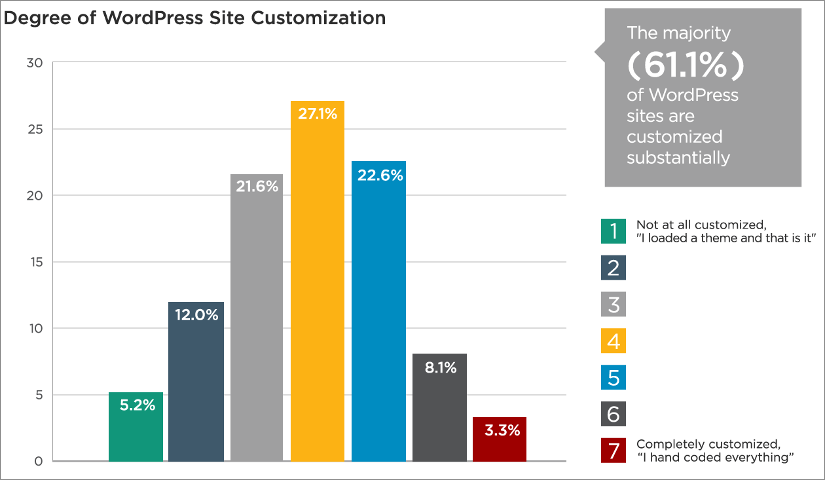
With a multitude of theme and plugin combinations, vulnerabilities continue to exist and new ones are constantly brought into the picture. Each new plugin is prone to adding additional vulnerabilities.
WordPress Vulnerabilities
There are three main components of WordPress that are important from a security perspective.
- Core – the basic default WordPress installation files that provide most of the functionality.
- Plugins – additional code to improve and extend the basic functionality.
- Theme – the presentation layer that may offer some limited extended functionality.
A point to note is that WordPress security vulnerabilities go beyond the core into the third-party themes or plugins. Notably, a recent report by wpscan.org, states that from the 3,972 known WordPress security vulnerabilities:
52% are from WordPress plugins
37% are from core WordPress
11% are from WordPress themes
The goal of a website hacker is to gain unauthorised access to your WordPress site with administrative access. You can do this from the WordPress dashboard or on the server-side by inserting scripts or files. Also, hacking may not always be done by a person. The terms given below usually describe the hacking system:
The terms mentioned below mostly describes the hacking system:
- Single Bot is an automated computer that can attack one site at a time or a small number of sites simultaneously. The attacks are usually unsophisticated attacks.
- A Person who goes into hacking systems manually attacks one site at a time. This method is slow but comprehensive.
- A Botnet is a group of computers that at the same time attack multiple sites rapidly. These attacks are unsophisticated but a large number of computers with multiple IPs add to the complexity.
There are two primary types of attacks that can take place against WordPress websites:
Non-targeted automated attacks are generic and take advantage of a known vulnerability. Ahese attacks may work by scanning a range of IP addresses. The automated system looks for a specific version of WordPress or a plugin. Mostly, these versions are most prone to a potentially exploitable vulnerability.
Targeted attacks happen when a hacker targets a website specifically. Notably, popular websites are most likely to be the target of hackers.
Listed below are the common security issues and risks associated with WordPress:
1. Brute Force Attacks:
These attacks refer to the repetitive entering of multiple usernames and password combinations until the attack is successful. The brute force attack method exploits the WordPress login screen to get access to the website. WordPress, by default, doesn’t limit login attempts. Bots can attack the WordPress login page using the brute force method.
2. File Inclusion Exploits:
A WordPress website runs at the backend on PHP code. Vulnerabilities in the PHP code are the next most common security issue with WordPress. File inclusion exploits occur if someone is using a vulnerable code to load remote unsafe files. These allow hackers to gain access to the website and its wp-config.php file.
3. SQL Injections:
WordPress uses SQL to query the database. This makes it vulnerable to SQL Injection Attacks. SQL injections occur when an attacker gains access to the WordPress database and the website data. He may be able to create a new admin user account. He can then log in and get full access to the WordPress website. SQL injections may also insert new data into the WordPress database such as links to malicious or spam websites.
4. Cross-site Scripting (XSS):
The most common vulnerability found in WordPress plugins, XSS vulnerabilities are very common and likewise complex. The attacker gets an innocent victim to load web pages with insecure JavaScript scripts. These scripts allow stealing the data from vulnerable WordPress website.
5. Cross-site Request Forgery (CSRF):
A hacking mechanism tricks a user into performing an unwanted action. This usually is done from within a web application, in which the authentication is done. For example, a phishing email with a link to a page that would delete a user’s account in the WordPress admin.
6. Malware:
Malicious software or Malware is code that can gain unauthorised access to a website and gather sensitive data. With thousands of types of malware infections on the web, WordPress is not vulnerable to all of them. The four most common WordPress malware infections are:
- Backdoors
- Drive-by downloads
- Pharma hacks
- Malicious redirects
Hardening WordPress Security
The first set to hardening WordPress security is to keep the website up-to-date and aware of the latest vulnerabilities. You will then be able to update your site for every new vulnerability. But updating WordPress is not enough. There are more issues to handle to be able to truly secure your WordPress websites.
What Needs to be Protected?
It is just not about protecting the website and its files. The user or customer data is most crucial and needs security as well as protection. The WordPress MySQL database is the backend for WordPress and stores this data.
You need to primarily protect the customers’ data. If the website is insecure, it is prone to hacking, as a result, the data becomes impossible to recover.
Next, you need to protect your website. This includes protecting the website files also. It would be disastrous if an attacker is able to read or modify your website files or source code. They can collect user data and also gain admin login access. Once the files are compromised the user data gets compromised too.
Methods for Hardening WordPress Security
As we have discussed above, security practices are many both for beginners and advanced users. The key is to identify WordPress vulnerabilities and adapt techniques and tools to get around them. The article here discusses some of the potential WordPress vulnerabilities and countermeasures for them. What we do below is a quick walk-through of the basic techniques for hardening WordPress security. We then elaborate on the advanced issues and how to tackle them with slightly more effort.
10 Easy ways for hardening WordPress security for DIY Users
Backup your website:
The most important thing is to backup your website data on a regular basis. If your website is hacked you can restore your WordPress site from a non-infected backup. It is also critical to store the backup data at a trusted location. You also need to take care and remove all old backups of the site from your website.
Pick a solid WordPress host:
Selecting a WordPress Host gives the option to choose from shared-hosts, managed-hosts and a number of other variations. It is important to set up proper permissions on your server and follows proactive security practices. Server hardening is an important component of hardening WordPress security. By all means, security measures at both hardware and software level are a must in IT infrastructure hosting WordPress sites. Pick a reliable hosting company and choose wisely when you decide how to host your website.
Use reputable Themes and Plugins:
Download add-ons for your site from reputable sources as it reduces the scope for potential hackers. The most popular WordPress plugin or theme developers get a third-party audit from a company like Sucuri prior to release. Vulnerabilities can occur in these plugins also. However, these developers are expected to be more proactive in their approach to security.
Use Secure Protocols:
Communication between the web server and the browser must be done on secure protocols. Using HTTPS enables encrypted communication between browser and web server. You can follow your hosting provider’s instructions to enable HTTPS. Once HTTPS is enabled, you need to edit the “.htaccess” and the “wp-config.php” file as per the information here. Use sFTP in place of normal FTP for file transfers and other commands. The sFTP protocol uses strong encryption to sign in and works on SSH which is already installed on most web servers.
Change the WordPress Login URL:
A WordPress site’s default login URL is domain.com/wp-admin. This is also known to the bots, hackers, and hacking scripts. You can change the URL and be better protected from brute force attacks. Also, you can change the WordPress login URL from the “General” section in settings.
Use a Strong Username & Password:
Being a WordPress admin it is important to follow good WordPress password security practices. Use strong passwords, do not share passwords and changing passwords regularly are some of the easy to follow rules.
Enable WordPress Two-Factor Authentication:
It is also crucial to make login to all your accounts challenging as possible. Use unique, and difficult to guess usernames and passwords across all your accounts, not just your WordPress login. With Two-factor authentication other than the password, one needs an additional time-sensitive code to log in. This method is one to lock down the WordPress login. It almost minimises the potential of successful brute force attacks.
Limit Access to Vital Parts of your WordPress Website:
- Manually change the default WordPress in the” wp-config.php” file.
- Secure your “wp-config.php” file by moving it from the default location like one directory above the WordPress installation. To move the wp-config.php file copy everything to a different file. In the wp-config.php file add a PHP include statement to include the other file.
- Secure the “.htaccess” file by adding allow and deny rules to it.
- Turn off XML-RPC in the “.htaccess” file. Keeping the XML-RPC enabled is the cause of Brute Force attacks and Denial of Service attacks. Preferably turn off XML-RPC in the settings altogether.
- Change directories and files to have the correct permissions both on the WordPress installation and on the webserver. Set the permissions on the wp-config.php file to 440 or 400 to prevent other users from reading or writing to it.
Now you need to Add Server Access Control:
- In the default mode, WordPress runs as apache/apache, which is the default web server role. Try to create a new user that will be the default and disallow the rights to the webserver user.
- Assign appropriate user roles. Don’t assign an administrator role unless a person actually requires admin functionality. Admin privileges provide a lot of added permissions. Use the different degrees of roles and permissions provided by WordPress and restrict user access to sensitive data. This would keep you protected from “sensitive data exposure”.
- Password protect the “wp-admin” directory. Add an extra layer of authentication to protect the “wp-admin” directory apart from the login password. More details on how to do this can be found here.
- Disable directory browsing in WordPress. Disable the File Editor in the WordPress Admin panel. Hackers also usually try to edit PHP files or themes using the Appearance Editor. Add the ‘DISALLOW_FILE_EDIT’ rule in the wp-config.php file. Hackers will not be able to access files without FTP access.
Run scheduled malware scans:
Keep tabs on potential malware infections with scheduled malware scans. Most scan tools give you a report on the website’s malware status.
Keep your WordPress site updated:
Keep your WordPress site updated to avoid potential WordPress security issues. Also, if there are any premium WordPress plugins or themes installed keep them updated. Consequently, ensure to renew the license to get updates.
Use a WordPress Security Plugin:
Use a WordPress security plugin for your WordPress website. Most security plugins offer options to set important and recommended WordPress security settings. Moreover, it is easier and safe to rely on a one-stop security solution. Some of the popular plugins available are:
- iThemes Security: This plugin is available in both a free and premium version. iThemes provides over 30 different ways for hardening WordPress security.
- WordFence: This is another security plugin in both a free and premium version. With over 11 million downloads, WordFence has a strong user base.
- Sucuri: Sucuri maintains a free plugin in the WordPress repository. They also provide a more comprehensive plugin for malware and blacklist scanning, DDoS protection, malware cleanup etc. The Sucuri service also includes a cleanup option if the site is compromised.
Advanced Hardening WordPress Security Methods
The Current OWASP Top 10
- A1 – Injection
- A2 – Broken Authentication and Session Management
- A3 – Cross-Site Scripting XSS
- A4 – Insecure Direct Object References
- A5 – Security Misconfiguration
- A6 – Sensitive Data Exposure
- A7 – Missing Function Level Access Control
- A8 – Cross-Site Request Forgery
- A9 – Using Components with Known Vulnerabilities
- A10 – Invalidated Redirects and Forwards
The chart below shows the spread of the most common vulnerabilities trends and the security risk of the applications.
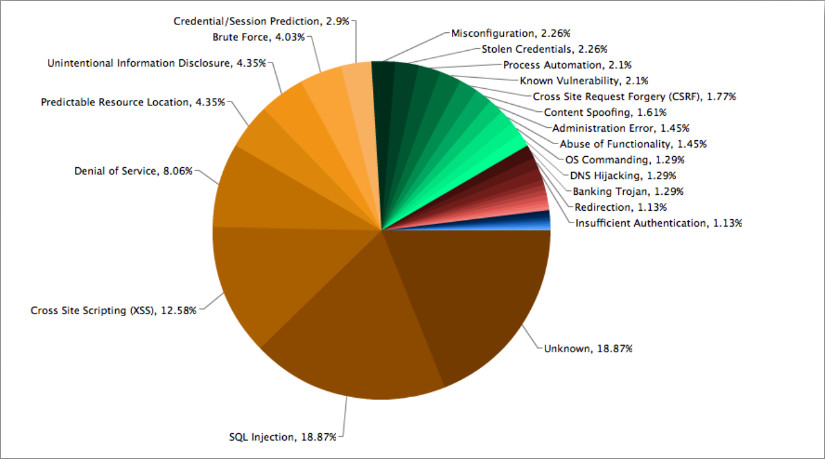
Note that 32% of these attacks are from A3 – Cross-Site Scripting XSS or A1 – Injection. 20% of the attacks are by unknown methods which do not give any data for the background of the attacks. The rest of the attacks are due to miscellaneous methods, many of which are in the OWASP Top 10. You can read more about these security risks at the OWASP listing for Top 10 -2013.
We know that WordPress is quite secure as long as developers follow standard security practices. The tips mentioned ahead are for added security and are advanced methods of hardening WordPress security. Most of these techniques are complicated and you need to understand them well. It is strongly recommended to first test these on a test site. The coding details of most of these methods can be found here.
We know that WordPress is quite secure as long as developers follow standard security practices. The tips mentioned ahead are for added security and are advanced methods of hardening WordPress security. Most of these techniques are complicated and you need to understand them well. It is strongly recommended to first test these on a test site. The coding details of most of these methods can be found here.
1. Disable HTTP Trace Method
The Cross-Site Tracing (XST) and the Cross-Site Scripting (XSS) attacks target systems that have the HTTP TRACE functionality. HTTP TRACE is a default functional feature on most web servers and is used for things like debugging. Hackers who use XST typically steal cookies and other sensitive information using header requests. You can disable the trace functionality by adding the following in your .htaccess file:
RewriteEngine On
RewriteCond %{REQUEST_METHOD} ^TRACE
RewriteRule .* - [F]2. Remove Header Outputs from your WordPress Installation
WordPress at times adds a lot of output in the header. This output is specific to the various services that are part of WordPress. To remove this output, add the following code to your theme’s “functions.php” file:
remove_action('wp_head', 'index_rel_link');
remove_action('wp_head', 'feed_links', 2);
remove_action('wp_head', 'feed_links_extra', 3);
remove_action('wp_head', 'rsd_link');
remove_action('wp_head', 'wlwmanifest_link');
remove_action('wp_head', 'parent_post_rel_link', 10, 0);
remove_action('wp_head', 'start_post_rel_link', 10, 0);
remove_action('wp_head', 'adjacent_posts_rel_link_wp_head', 10, 0);
remove_action('wp_head', 'wp_generator');
remove_action('wp_head', 'wp_shortlink_wp_head', 10, 0);
remove_action('wp_head', 'noindex', 1);3. Change your default WordPress DB prefix
WordPress uses a default prefix value of “wp_” for the DB tables. This can be used by malicious bots and hackers to guess your DB table names. Changing the WP DB prefix value is much easier to do at installation time because it is set in the wp-config.php file. However, if the site is already live then the method is more complicated.
- Do a full database backup and save the backup somewhere. You may use a backup tool for this.
- Do a complete dump of your WordPress database using “PHPMyAdmin” into a text file. You may also take a backup of this text file.
- Replace all instances of “wp_” with your own prefix using a code editor.
- In the admin panel, deactivate all plugins.
- Using the “PHPMyAdmin”, remove the old DB and import the new one using the file edited in step 3.
- Edit the wp-config.php file with the new DB prefix value.
- Re-activate the WP plugins
- Perform a save on the permalink settings by going to Settings->Permalinks. This would refresh the permalink structure.
4. Deny Potentially Dangerous Strings
Identify the potentially dangerous query strings. Add the following code in your .htaccess file to help prevent XSS attacks. This set of rules will strip the URL requests of many dangerous attack injections. You can add more strings here though we have included the common ones. Note that the functionality of some plugins or themes could break if you do not exclude strings that are used by them.
<IfModule mod_rewrite.c>
RewriteCond %{REQUEST_METHOD} ^(HEAD|TRACE|DELETE|TRACK) [NC]
RewriteCond %{QUERY_STRING} ../ [NC,OR]
RewriteCond %{QUERY_STRING} boot.ini [NC,OR]
RewriteCond %{QUERY_STRING} tag= [NC,OR]
RewriteCond %{QUERY_STRING} ftp: [NC,OR]
RewriteCond %{QUERY_STRING} http: [NC,OR]
RewriteCond %{QUERY_STRING} https: [NC,OR]
RewriteCond %{QUERY_STRING} mosConfig [NC,OR]
RewriteCond %{QUERY_STRING} ^.*([|]|(|)|<|>|'|"|;|?|*).* [NC,OR]
RewriteCond %{QUERY_STRING} ^.*(%22|%27|%3C|%3E|%5C|%7B|%7C).* [NC,OR]
RewriteCond %{QUERY_STRING} ^.*(%0|%A|%B|%C|%D|%E|%F|127.0).* [NC,OR]
RewriteCond %{QUERY_STRING} ^.*(globals|encode|config|localhost|loopback).* [NC,OR]
RewriteCond %{QUERY_STRING} ^.*(request|select|insert|union|declare|drop).* [NC]
RewriteRule ^(.*)$ - [F,L]
</IfModule>5. Apply PHP Hardening to your System
You can install and enable a PHP hardening system on your server. This can further increase the security of the system by protecting against various vulnerabilities.
6. Don’t Let the Hackers Know Your WordPress Version
It is important to hide the version of WordPress you are using from hackers. If it is publicly available, it would help hackers identify the vulnerability they can use to hack the site. WordPress 2.6 and above automatically adds the version in the WP_head section. However, you can remove it in the header.php file.
7. Lock-out Users with Failed Login Attempts
It is still possible that even with so much password protection, hackers may still find ways to crack the password of your WordPress admin. Let us see how login lockdown works. If a user makes too many failed login attempts, they will immediately be logged out from logging in to the site for the next few hours. This feature is available with most security plugins in WordPress. This is one of the effective defences against brute-force attacks.
Checking if WordPress Site is Hacked or Not
We know that even the most alert system administrators will not be able to constantly monitor their site. Even the best monitoring tools may have a delay between each site scan. There are various ways you can use to detect if your site has been hacked.
- Your browser would in most cases alert you about the hack.
- Your hosting provider takes your site offline because it is hacked.
- Google search results flag your site as hacked or harmful.
- Google’s search console alerts you to malware on your site.
- Your malware scanner alerts you to an infection or hack.
- A customer contacts you about your site being hacked.
- Use a source code scanner to detect a hack.
- Use a monitoring service to detect if more than a very small percentage of the page has changed.
- Monitor site traffic and watch for increasing activity spikes.
- Visit your Site Regularly for sanity checks.
- Use a Remote Scanner that looks at the HTML that your site produces. This detects a hack if the hacker includes malware in the HTML.
More details on these methods can be found here.
Fixing Hacked WordPress Site
So can you really fix a hacking of the WordPress site or do you lose the entire data after the hacking? A hacked website can be easily recovered; let us see how it can be done:
- Restore your website from backup if available. Change all passwords immediately.
- If you can log in to the site as admin, then remove the hacked files and seal the point of entry.
- Scan and remove malware.
- If you cannot log in to the site then ask for help from your web host.
- Backup important files and reinstall WordPress.Contact professional services if you cannot do anything to restore your site.
- Contact professional services if you cannot do anything to restore your site.
Hardening WordPress Security Best Practices: Risk Reduction over Risk Elimination
We have looked at the methods to improve the security of your WordPress sites. It is a well-known fact that risk reduction wins over risk elimination. Risk reduction is proactive and will keep you safe in all scenarios. Thus security is about risk reduction, not risk elimination since risk will never be zero. You should deploy security controls that best address the risks and threats.
Let us now collate the security best practices which if followed will result in hardening WordPress security. These best practices will surely protect your site from possible attacks and vulnerabilities.
- Make WordPress core code updates quickly. You can also auto-configure the updates.
- Proactively upgrade plugins and themes as new versions become available.
- Prevent sniffed login attempts by adding password protection.
- Enforce strong passwords.
- Actively block and log incoming security attacks.
- Ensure proper file permissions, isolate sites, and decouple databases.
- Conduct frequent, proactive vulnerability and malware scanning on all systems.
- Perform regular penetration tests by independent security experts. Track remediation of the findings of these test. Train application developers and architects in secure development.
- Apply procedures for secure development.
- Report Bugs and Vulnerabilities.
- Keep track of Zero-day vulnerabilities. If it is zero-day, then you need to work closely with the vendor to find out when a fix will release and then apply that fix.
Bonus: Check out this Security Index developed by Brian Jackson at Kinsta which is indeed one stop for all your WordPress security requirements.
Hardening WordPress Security – Being Aware and Involved
We know by now that WordPress security is an ongoing activity. You need to work towards hardening WordPress security and keeping your WordPress sites secure. This would be a contribution towards the prevention of malicious activity. These activities can harm websites, web servers, users’ PCs, tablets, and other smart devices.
WordPress is a popular CMS and knowledge about WordPress security is widely available. Being aware of the security hardening practices and putting them in your workflow is a must. While running maintenance on your website and web server remember to be secure. You will not only have proper control over your web content but also do your part to make the Internet a secure place. Always remember. Check out best WordPress firewall plugins, best WordPress security plugins, Sucuri vs Cloudflare, CDN services.
[bctt tweet=”SEC_RITY is incomplete without “U” (you).” username=”templatetoaster
How TemplateToaster Website Maker Helps in Hardening WordPress Security?
Developing robust security for WordPress sites can be a daunting task. It is difficult to keep everything in mind whether you do it alone or with a secure partner. WordPress requires active hardening security management. Hardening WordPress security is critical for site security and success.
Developers can opt for a managed WordPress platform or tool to comprehensively ensure the hardening security of their WordPress environments. TemplateToaster, a web design software is popular for developing secure websites across multiple CMS including Joomla, Magento, Drupal and Prestashop. WordPress themes developed with TT are secure and as per WordPress standards. Incorporating TemplateToaster in your workflow will give you a range of securely implemented themes to work with. Therefore you get to be on the safer side that your WordPress security will further get better with the themes created using this tool.
Related Articles:
How to install WordPress theme, How to find WordPress login Url, How to change WordPress language, How to Move WordPress from Localhost to Live Server, How to Create a WordPress Custom Login Page?
Build a Stunning Website in Minutes with TemplateToaster Website Builder
Create Your Own Website Now
Security of the website is most important. If security is not done than the google will start sending warning messages.